News
Ransomware attacks vulnerable computers around the world and disrupts many institutions and organizations

What happened?
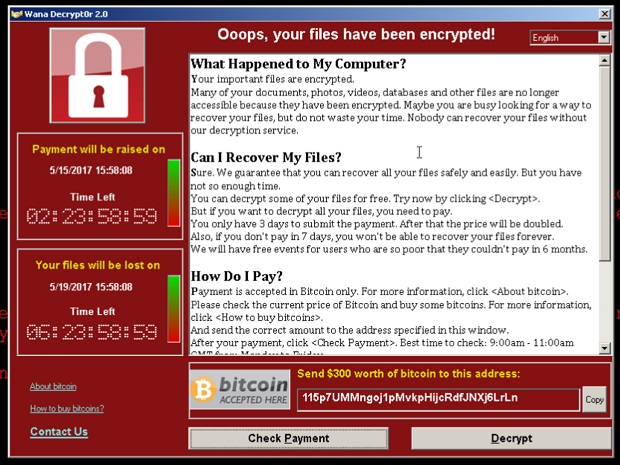
Last Friday, May 12th, 2017, a type of malicious software code (malware in short) named Wanna Cryptor found its way to affect computers around the world that are running older versions of Microsoft Windows Operating System or newer versions which have not applied the latest security updates issued by Microsoft. More than 40,000 computers were compromised and their data files were locked. The users were asked to pay a ransom of $300 to de-encrypt the information saved in their computers.
It also started spreading over The Internet to other vulnerable connected computers. As at Monday morning; about 200,000 computers are affected in more than 150 countries.
No doubt an in-depth analysis will place a figure on the financial cost (lost productivity, lost revenues, and the least of it – paid ransom) in the coming weeks.
Image credit: Cisco Talos Intelligence blog
This attack shows the ubiquity of the internet and technology in general; such attacks may have significant adverse effects in our daily lives in the hands of criminals.
In this instance the attack was opportunistic and did not necessarily target a specific country or a specific organization. However, as connectivity extends and the number of online applications increases, the targeted cyber-attacks will also be inevitable and a new type of warfare may enter our lives. Smart phones may initiate random network activity; intelligent cars may drive against the drivers’ wills. The effects could be disastrous from a total network congestion to loss of lives.
Why it happened?
The irony of this attack goes back to February 2017 when it was revealed that the United States National Security Agency (NSA) had identified a security vulnerability in Microsoft Windows operating system software. It is not clear when this vulnerability was identified originally and why the NSA kept it secret. One explanation is perhaps the intention of the NSA to use this vulnerability to access computers for national security purposes.
Once the news about this vulnerability was made public, in March 2017, Microsoft issued a fix for all Windows software versions that are within their regular support phases (Windows 7 and later versions)[1]. A fix was not released for earlier versions where the support had expired (Windows XP is an old version and widely used around the world despite no longer being supported by Microsoft).
On April 8, 2017 another interesting development took place and a group of hackers, known as Shadow Brokers, announced that they have access to an encrypted cache of “software hacking tools” and released a password for the cache on The Internet[2].
It was only a question of when, not if, a malicious attack would occur once these tools were publicly available.
Who was affected?
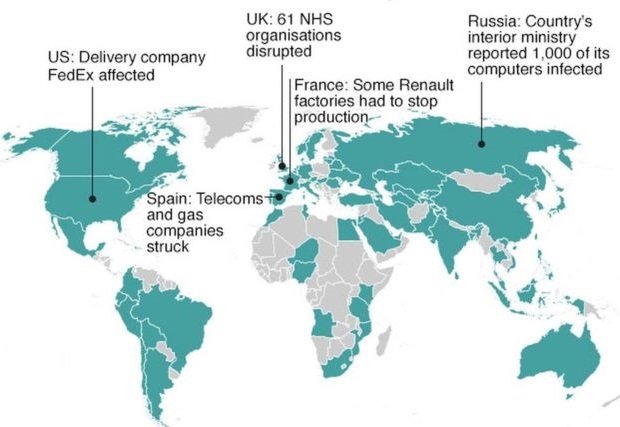
The diversity of the organizations affected by this attack is phenomenal. Services stopped, manufacturing halted, routine activities were disrupted. In more than 150 countries about 200,000 computers were reported to be hit by the attack.
Below are just a few examples collated from some of the global news sources.
-
Hospitals and National Health Service (NHS) trusts in the United Kingdom
-
Telecommunications Company (Telefonica) in Spain
-
Government Departments and Hospitals in China
-
Transport and Logistics company FedEx in the USA
-
Hospitals in Indonesia
-
More than 1,000 computers in the Interior Ministry in Russia
-
2,000 computers in 600 organizations in Japan
-
Police Department in Andhra Pradesh and several companies in major cities of India
-
Car manufacturing plants in France
-
Gas companies in Spain
-
Electronic boards at railway stations in Germany
Image credit: http://www.bbc.com/news/world-39919249
What can be done now?
Microsoft took the unprecedented step to issue a software patch for the old versions of their Windows Operating Systems (Windows 8, Windows XP); and server software[3].
Individuals and organizations can protect their computers and networks to the best of their ability, by
-
Contacting their IT services and support specialists for advice
-
Ensuring the software used in their networks is current and up to date with all the security patch software from the vendors are applied
-
Being extremely careful of the current Wanna Cry, or Wanna Crypt, or Wanna Decryptor variations of the ransomware (never clicking on any enclosure files in any email messages)
What can be done in the future?
The most important precaution to protect “connected computers” from malicious software attacks
-
Design and implement necessary software firewalls where these network based attacks can be blocked before reaching the individual computers
-
Always apply security patch software updates from computer and networking software vendors
-
Do not use any software programs once their support periods are expired
[1] https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
[2] http://www.bbc.com/news/technology-39553241
[3] https://www.catalog.update.microsoft.com/Search.aspx?q=MS17